My users receiving lot mails from no-reply@mydoman.
senderEmail(2): no-reply@****group.org parsed using: "****group ." <no-reply@****group.org> is being treated as from: no-reply@****group.org which is wrong.
These message are getting quarantined by ClamAV. What if the mail passes ClamAV and goes to customer inbox/spam ?
How to reject these mails reaching the spool ?
EMail Header
Return-Path: <>
Received: from [10.88.0.3] (17.205.73.34.bc.googleusercontent.com [34.73.205.17]) by mx-ids-4.idslinfo.com with SMTP;
Wed, 16 Jul 2025 08:50:10 +0530
Content-Type: multipart/related; boundary="===============1753619820824428618=="
MIME-Version: 1.0
From: "****group ." <no-reply@****group.org>
To: *********@****group.org
Subject: =?utf-8?q?**Action_Required=3A_Your_Mailbox_is_full?=
X-Priority: 2
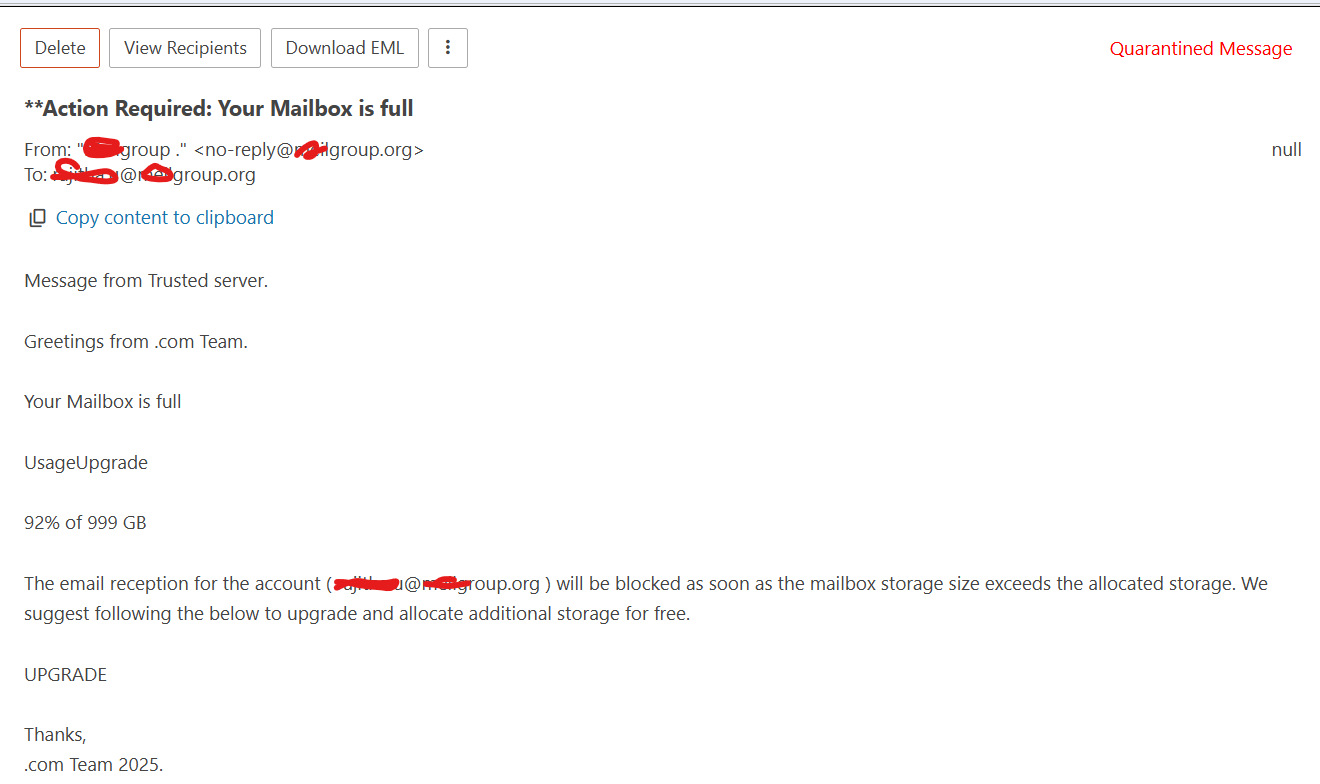
Message Text
Message from Trusted server.
Greetings from .com Team.
Your Mailbox is full
UsageUpgrade
92% of 999 GB
The email reception for the account ( *********@****group.org ) will be blocked as soon as the mailbox storage size exceeds the allocated storage. We suggest following the below to upgrade and allocate additional storage for free.
UPGRADE
Thanks,
.com Team 2025.
SMTP Logs
[2025.07.16] 08:50:09.631 [34.73.205.17][43389284] Connection initiated
[2025.07.16] 08:50:09.637 [34.73.205.17][43389284] rsp: 220 mx-ids-4.idslinfo.com
[2025.07.16] 08:50:09.638 [34.73.205.17][43389284] connected at 7/16/2025 8:50:09 AM
[2025.07.16] 08:50:09.638 [34.73.205.17][43389284] Country code: US
[2025.07.16] 08:50:09.852 [34.73.205.17][43389284] cmd: ehlo [10.88.0.3]
[2025.07.16] 08:50:09.857 [34.73.205.17][43389284] rsp: 250-mx-ids-4.idslinfo.com Hello [34.73.205.17]250-SIZE 104857600250-AUTH PLAIN250-STARTTLS250-8BITMIME250-SMTPUTF8250-DSN250 OK
[2025.07.16] 08:50:10.072 [34.73.205.17][43389284] cmd: mail FROM:<> size=12821
[2025.07.16] 08:50:10.078 [34.73.205.17][43389284] senderEmail(1):
[2025.07.16] 08:50:10.090 [34.73.205.17][43389284] rsp: 250 OK <> Sender ok
[2025.07.16] 08:50:10.090 [34.73.205.17][43389284] Sender accepted. Weight: 0. Block threshold: 30.
[2025.07.16] 08:50:10.306 [34.73.205.17][43389284] cmd: rcpt TO:<*****@****group.org>
[2025.07.16] 08:50:10.308 [34.73.205.17][43389284] rsp: 250 OK <*****@****group.org> Recipient ok
[2025.07.16] 08:50:10.523 [34.73.205.17][43389284] cmd: data
[2025.07.16] 08:50:10.523 [34.73.205.17][43389284] Performing PTR host name lookup for 34.73.205.17
[2025.07.16] 08:50:10.523 [34.73.205.17][43389284] PTR host name for 34.73.205.17 resolved as 17.205.73.34.bc.googleusercontent.com
[2025.07.16] 08:50:10.529 [34.73.205.17][43389284] rsp: 354 Start mail input; end with <CRLF>.<CRLF>
[2025.07.16] 08:50:10.744 [34.73.205.17][43389284] senderEmail(2): no-reply@****group.org parsed using: "****group ." <no-reply@****group.org>
[2025.07.16] 08:50:10.777 [34.73.205.17][43389284] DMARC Results: Skipped (No Return Path), Reason: Unknown, Reject? False
[2025.07.16] 08:50:10.777 [34.73.205.17][43389284] rsp: 250 OK
[2025.07.16] 08:50:10.785 [34.73.205.17][43389284] Received message size: 12824 bytes
[2025.07.16] 08:50:10.786 [34.73.205.17][43389284] Successfully wrote to the HDR file. (d:/SmarterMail/Spool/SubSpool2/611974449166.hdr)
[2025.07.16] 08:50:10.786 [34.73.205.17][43389284] Data transfer succeeded, writing mail to 611974449166.eml
[2025.07.16] 08:50:10.992 [34.73.205.17][43389284] cmd: quit
[2025.07.16] 08:50:10.992 [34.73.205.17][43389284] rsp: 221 OK
[2025.07.16] 08:50:10.992 [34.73.205.17][43389284] disconnected at 7/16/2025 8:50:10 AM